|
How Hackers Choose Their Targets
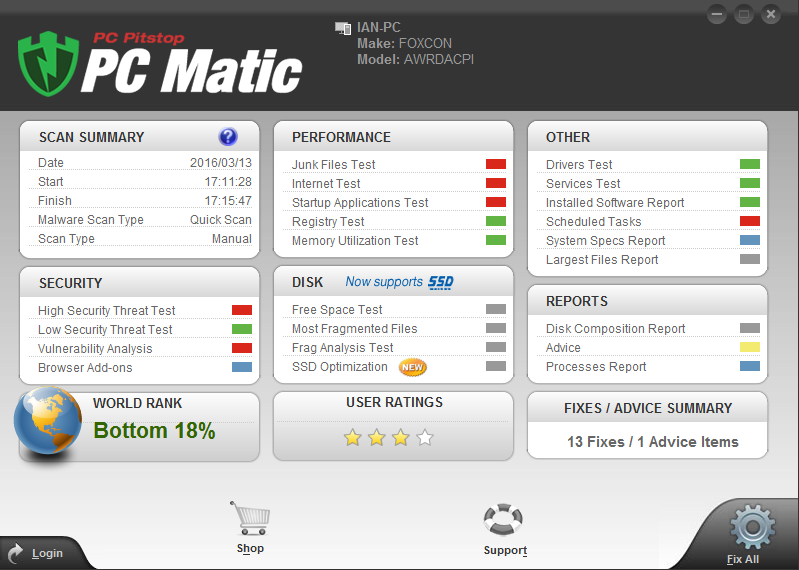
Hackers target vulnerable systems. There it is. That is the big secret, which likely isn’t as shocking as one anticipated. Why do hackers target vulnerable systems? This too is rather simple. They don’t want to have to “work” at hacking the system, they want users to leave the door open for them. And often times they are. Leaving third-party applications and operating systems outdated leaves endpoints and servers, as well as all the data on them, vulnerable to attack. It is imperative for users to update all devices in a timely manner. Often times this will take longer for larger businesses, as proper testing should be completed to ensure the update will not negatively impact the functionality of existing software or devices. That being said, the testing process should take place once updates are available, so updates can be installed as quickly as possible. It should also be noted, major software companies, such as Microsoft, have reoccurring update release dates. Therefore, IT professionals can schedule when testing will need to be completed with the predetermined update dates. Automate Updates? Users at a smaller scale, either home users or perhaps a smaller business may automate application and operating system updates to take the legwork out of manually launching the update. This feature is great for those who want to set it and forget it. However, users must remember to reboot their PCs every day. When updates are installed, they often are not finalized until the device is rebooted. Therefore, users may think they’re protected with the latest updates, but in reality, they haven’t finished installing because no reboot has been initiated. Rebooting is equally important for those who manually update as well. If it isn’t getting done — the update is NOT complete. Other Forms of Vulnerability Although unpatched systems were the primary security threat identified by IT managers, other vulnerabilities should be addressed as well. Additional factors to evaluate include multi-factor authentication, IoT devices, BYOD policies, and password strength.
Multi-Factor Authentication and Password Strength
First and foremost, no one should be able to access your network with one basic password. Employers should be employing a multi-layer authentication feature to access their networks. As a component of that, proper password regulations should be in place. This includes requiring passwords to be changed every 30-45 days, including specific characters and numbers, and offering a password vault for employees to track their passwords to prevent them from being written down or kept in a Word or Excel document. IoT and BYOD The Internet of Things (IoT) has taken over the world. We’re more connected now than ever, whether it is our smartwatches notifying us of text or calls, or checking emails through our phones. We often bring these devices with us to work and connect them to company networks. This creates a major problem. If these devices are infected with malware of any kind — viruses, ransomware, spyware, etc. this malware can now spread throughout the company networks. Also, the likelihood of these IoT devices having any form of security solution installed is minimal at best. They often do not come with any form of antivirus installed, and some devices are not compatible with security solutions at all. Therefore, having a solidified Bring Your Own Device (BYOD) policy is important. Employees should know what is allowed and expected, and what is not. This should include three major things. First, what devices are permitted to connect to the company’s networks. Second, the company needs to mandate a security solution is installed on all devices permitted to connect to company networks. Lastly, it must include disciplinary measures if the policy is not adhered to.
3 Comments
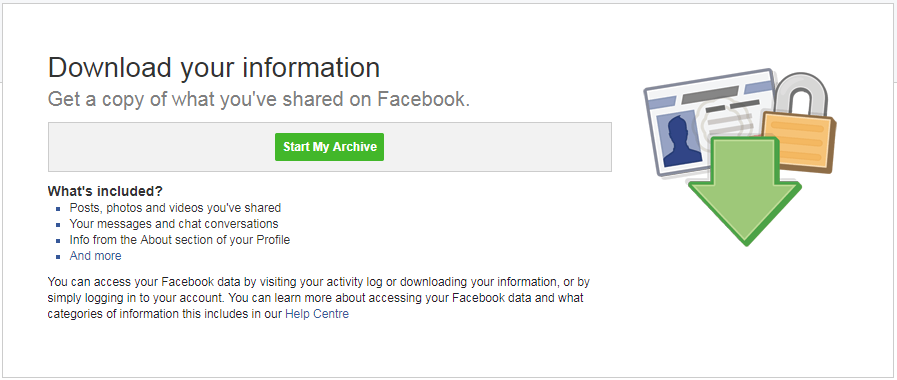
Find out if your Information was harvested from Facebook
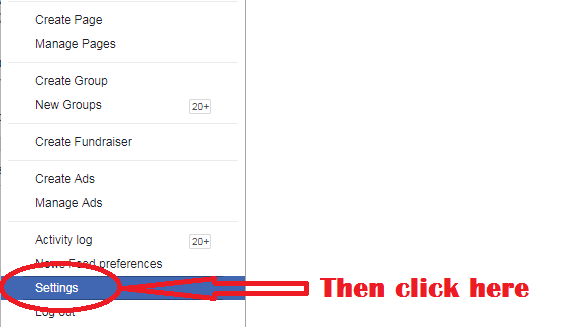
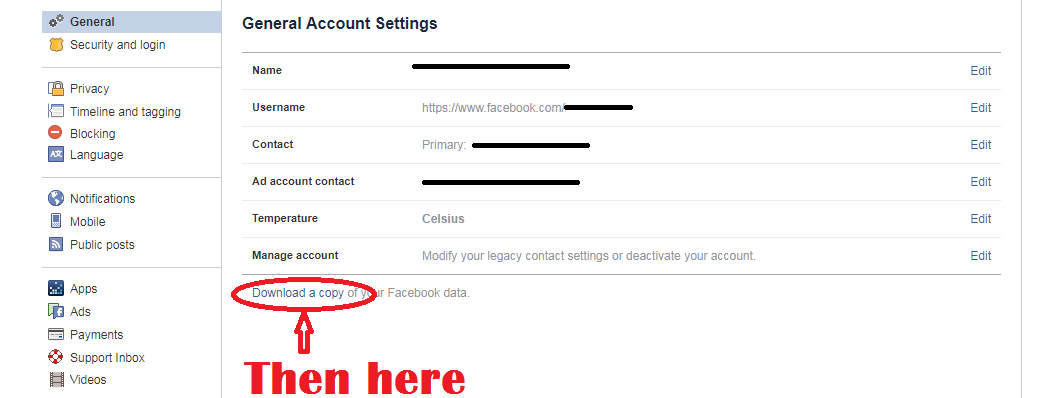
Facebook, continues to work toward rebuilding their brand after facing a major security scandal alongside London’s elections consultancy, Cambridge Analytica. Reports have confirmed personal data was harvested from the social media giant from Cambridge Analytica. It is believed, the election firm then used the data to show specific information on U.S. presidential candidates prior to the 2016 election. There are speculations that by segmenting the content shown to different Facebook users based on their personal information, their perceptions of the election candidates were impaired. Therefore, theoretically this may have made voters vote a different way than had they never been shown the information segmented based on their personal information. Due to those concerns, some reporting outlets believe the U.S. election results were tampered with. Whether or not this is true, can be debated. However, what Facebook users must be concerned with is if their information was involved with this scandal. The likelihood of you, or someone you know being impacted is quite high, as reports have confirmed 87 million accounts were involved. To find out, you’ll need to log into your Facebook account. After doing so, you should go to this website. Roughly halfway down the page, you’ll see this “Was My Information Shared” box. Within this box, it will disclose whether or not your Facebook information was shared with Cambridge Analytica. source: PC Pitstop - take a free security and health check Do you know what data Facebook holds of you? Well there's an easy way to find out. Over the recent past - Cambridge Analytica have come under fire for their revelations about how they access our information and use it to their 'clients' advantage in helping the middle-grounders decide which way to vote, for example. Every time you install an app on Facebook, you will see that it needs your permission to access certain data from your account, such as contacts, phone numbers and location etc. Without accepting these conditions, the app will not be installed. Most of which are needed for the app to work - but others are for data collection. This data is then collected by the app company and probably sold to companies like Cambridge Analytica for later use. This collected data can be used to target specific adverts at you, already knowing what you like, where you go and your email address. While most people would expect Facebook to have data on how they use the apps, they're a little shocked to discover it has access to everything from all the contacts on their phone to a record of every text message they've ever sent or received, even if they don't use Facebook Messenger. But that's not all Facebook has. The information they collect can also contain the phone numbers of people who aren't even on Facebook! Google knows where you have been, how long you have spent there and what road at what time of the day. I did a blog on this >>here<<. Collectively, Facebook and Google know EVERYTHING about you. Google also knows the websites you go to, the searches you make - imagine if a single company had all of this information? Well, they already do. To find out what Facebook has on you, follow these simple steps below and download the zip file. If you can't open it, download 7-zip from here. FREE PC/LAPTOP security and stability scan If you see anything like this on your PC - read on.
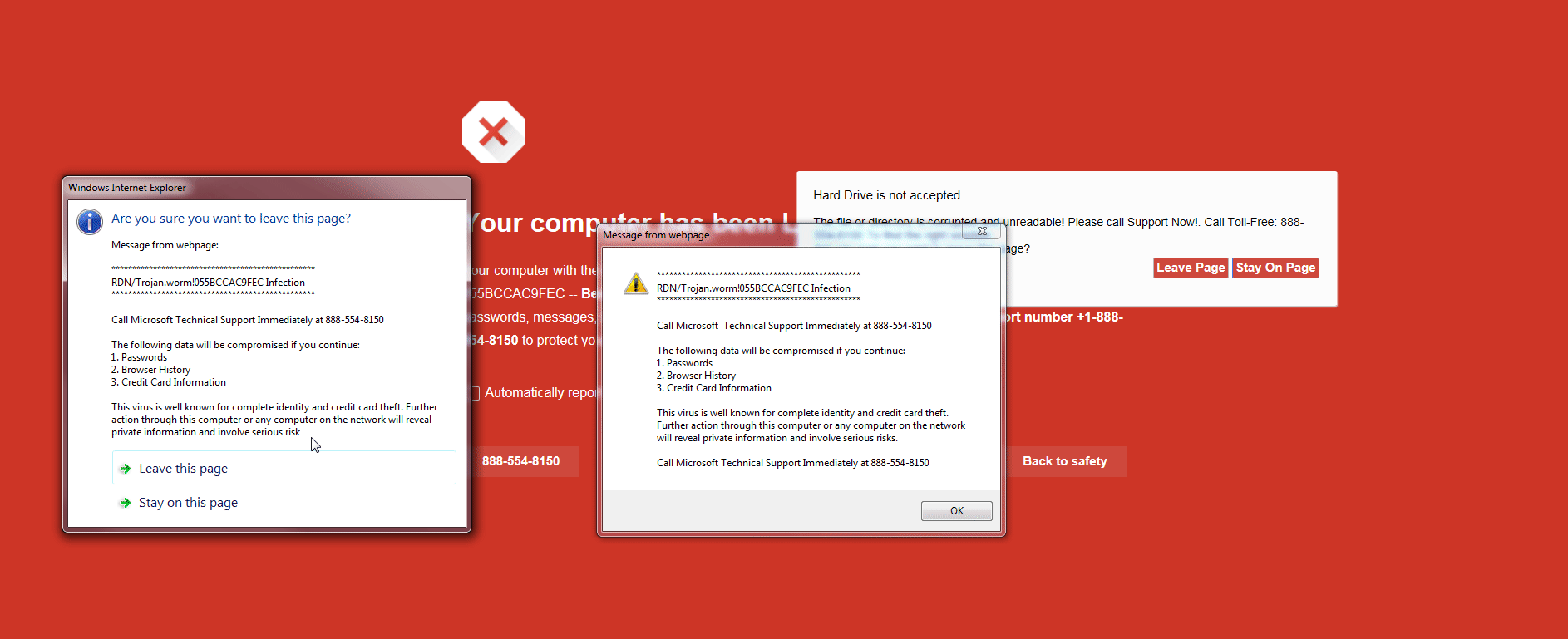
Web sites are being penetrated to display an infected page that places a Javascript alert inside an infinite loop. To the user, they are unable to escape from a dialog box and cannot navigate to other tabs. It appears as if the browser is locked. The page displays ominous warnings about virus infections, pornography, and lost personal information, frequently accompanied by a robo-voice reinforcing the message. To 'fix' the problem, users are urgently advised to call a toll free number. The call is transferred to India, where the attendant tries to gain control of the user's computer. Once inside, they display many false warning messages and finally try to charge between $400 - $600 to 'clean' the problem. PC Pitstop, the makers of PC Matic, has developed a technology to block the hoax and gather the telephone numbers the hoax is employing. Take look at PC Matic, who have targeted this kind of attack>>> pc-matic
A new scam is luring people into downloading ransomware. The scheme is targeting crypto-wallet users, and could also be spreading through phishing attacks. The scam is encouraging users to download a new form of crypto-currency that is bound to make them buku bucks. The fake crypto-currency, SpriteCoin, is just that — fake. When users click on what they think is the digital currency, they’re actually installing ransomware that begins encrypting their files.
Post encryption, users are told to pay .3 Monero. Monero is a legitimate digital currency, which is expected to be used more frequently moving forward and is worth approximate £100/$120 USD. So not only do you not get SpriteCoin, which was certain to get you rich, you instead find yourself infected and losing money. But it gets worse… Don't pay the ransom demands. It only encourages the cyber criminals to continue with ransomware infections if their successful with getting users to pay. It also puts a target on the user’s back for future infections. But beyond that, paying this particular ransom demand leads to additional issues. It may indeed get the files unlocked, but according to ZDNet, additional malware is then installed on the device. This malware includes the capability to enable the webcam, analyze images, and certificate harvesting. Reason enough not to pay the ransom? We hope so too. Stay safe, and watch out for quick “get rich quick” schemes like this. If it’s too good to be true, it likely is.
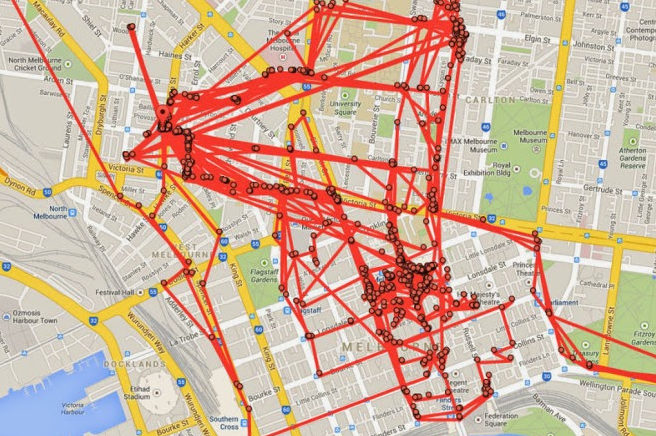
Did you know you can track your past movements through your Google account from your smart phone? Is that a good thing that Google has this info? To check this, I have looked back at some dates from 3 years ago and can tell exactly what time I arrived at certain destinations and how long I was there - 3 years ago!
Follow the link below and you will see some red dots on a map, simply zoom in, double click on one and in the left hand pane it will give you information about that journey and any pictures you took (if you store your pics on Google's cloud server - which I do). It's quite frightening really. It will only work however, if you have location services switched on on your phone and you are signed into Google on your phone. If you don't want Google to be able to track you - log out of Google on your phone until you need to be logged in! Check this out to see if your movements have been tracked by Google: https://maps.google.com/locationhistory/b/0it. Copy this link and SHARE on your timeline to let others know! > https://goo.gl/gK3FJD |
Archives
September 2018
Categories |